The Internet is a big old scary place, full of dark corners, strange protocols, dodgy individuals, unscrupulous corporations and cynical state-level actors.
The tools we use to access the Internet, though often very powerful, remain badly-designed. This is true not only in terms of the User Experience (UX) and User Interface (UI), but also in how they let us use and manage our data.
Most big Internet/Web companies use “dark patterns” to exploit normal human behaviors profitably, and often without serious consideration of the consequences to the average human psyche.
Every day there are hundreds if not thousands of severe security breaches, and every month or so we hear of egregious acts of deliberate abuse, or contemptible neglect on the scale of millions of individuals affected.
This is made worse by the sheer amount of data our devices leak, all the time. Pretty much every computer has a hardware backdoor, either explicitly as in the Intel Management Engine (perhaps added at the behest of the National Security Agency), and most mobile telephone modems are little black boxes over which the user has no control. Location, browser history, contacts, messages, emails, etc., etc,. are all leaked in multiple ways, through apps and websites, through wifi and 4G, and worst of all directly from the operating systems.
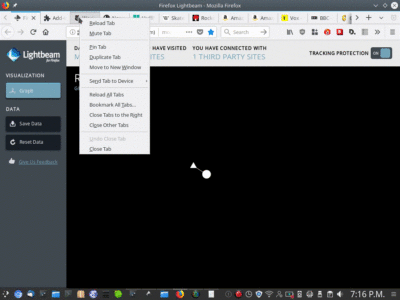
For example, in this video, we load the following sites simultaneously in a Firefox browser and use Lightbeam to visualise all the links made between sites by loading shared assets such as images, scripts, style sheets and other data common to any website.
Simulating a typical browsing session on 18 sites (nytimes.com, theguardian.com, huffingtonpost.com, en.wikipedia.orgi, skatehut.co.uk, amazon.com x 2, vox.com, bbc.com, cracked.com, facebook.com, trivago.ie, skyscanner.net, nbcnews.com, answers.com, weather.com, ie.match.com, imgur.com) you can see 384 different servsers now have data on how you access these websites. The extreme amount of inter-connectivity is quite a show!
Now we reload the same 18 pages with partial tracking prevention plugins to Firefox and observe only 58, and these only minimally.
What follows is a guide to ‘tightening up’. This advice is intended for personal use. It is broken down into sections so it can be implemented in stages. Each section is colour-coded according to difficulty as follows:
Easy – even for Grandpa
Normal – can set up email on phone
Hard – summon nearest teenager
Difficult – might need professional help
Problem: Hardware
At the bottom of the stack we have the hardware problem, which is that most computers are not totally under the control of their users, and usually have at least one but often two or more completely independent, remotely-controlled, onboard computers. On Intel chips it’s called the Intel Management Engine, on AMD it’s called the AMD Platform Security Processor. Most mobile telephones use a proprietary technology from Broadcom, a massive US company, and are made in China, and are known to have a variety of intentional holes in their security.
Solution: Use AMD products on the Laptop/Desktop and wait for Purism Mobile (and verified RISCV in the long term).
AMD make all the main desktop/laptop/server chips that are not made by Intel, and have a better reputation.
The Purism mobile project (Librem 5) is the great hope for everyone interested in fully user-controlled mobile phone. It will hopefully be ready in about a year. RISCV is a completely open, community-created, modern-chip-architecture that promises high-performance in both number of computations per second and energy use.
Problem: Operating System
Here we get to the big one, the choice of “church”. There are four main options: Apple, Google, Microsoft, GNU/Linux.
Apple is the most cultish OS, a mono-aesthetic walled garden, famous for its ‘taste’ and convenience, infamous for its rigidity and cost. They manage their app store jealously, refusing programs that interfere with their ability to profitise your time on their systems. They have a well-funded reputation for safety, frequently destroyed for those in the know by errors such as the ability to login in remotely as administrator without a password. Their mobile efforts are more secure in some ways, but Apple themselves still extract huge amounts of ‘telemetry’ on every user, for their own and others benefit.
Google offer Android. Google make money by selling advertising to third parties, along with detailed information about how to use best their platform. Android, though quite secure in certain aspects from a technical point of view, is still essentially a mobile person monitoring device. Google recently removed their famous “Don’t be evil” motto from their handbook.
Microsoft sell Windows 10, the latest version of the most widely and successfully attacked operating system ever. Microsoft have been in trouble all over the world for their antics. Their devices send vast amounts of ‘anonymized’ data back to headquarters deliberately, and to pretty much every major Internet crime group as well.
GNU/Linux is a multi-decade community-driven operating system initiated by one of the true heroes of privacy and freedom: Richard Stallman. It is now developed all over the world, in the open, by companies such as Google (who use it internally to power their advertising thought-trap) and organisations such as CERN and NASA. It powers most of the Internet, and is freely used on everything from wireless routers to phones to laptops to supercomputers.
Solution: Linux Mint, the easiest and most polished operating systems distribution (free as in speech and as in beer)
Difficult, but not impossible
Problem: Safe Browsing
We use a browser for nearly all our general use of the Internet. This is great as it provides an all-in-one tool that can do everything from email to games, but distressingly insecure as it is a one-stop-shop for tracking people’s habits online. There are four main browsers, each associated with one of the operating systems listed above.
- Apple – Safari (also runs on Microsoft)
- Google – Chrome (also runs on Apple, Microsoft, GNU/Linux)
- Microsoft – Edge
- Gnu/Linux – Firefox (also runs on Apple, Google, Microsoft)
Solution: Firefox and Tor Browser Bundle
Only one choice here, but it comes in two varieties: Firefox, and Firefox packaged as the Tor Browser Bundle.
Firefox is a powerful, research-driven, privacy-focussed, standards-compliant, community-backed browser. All the code is open-source, meaning is can be and is examined out in the open by experts all over the world. The non-profit organisation that oversees Firefox, Mozilla, is very clear in its motives. The Tor Browser Bundle wraps the browser with the Tor project, providing vastly increased anonymity online, at the expense of being slower to use due to the added encryption complexity.
Firefox is better with plugins, here are a few to get you started (these can break many websites):
- Disconnect
- Multi-Account Containers
- HTTPS Everywhere (can break many websites, including this one)
- Privacy Badger
- Temporary Containers
- uBlock Origin
- uMatrix
Problem: Your Internet Service Provider/Mobile Phone Operator
Companies that sell you Internet Access are almost all required by law to record a lot of data about your activity.
Solution: A Virtual Private Network such as Proton VPN
A VPN sets up an encrypted point-to-point link from your computer/phone to another computer in a server farm elsewhere on the Internet. This hides your IP address (one of the most important tracking details), and some other data.
Solution: Use TOR
TOR is a method of encrypting your network traffic over a randomised colection of links over the Internet. It is quite secure, more so than only a VPN, but really quite slow. Used with a VPN (computer -> VPN -> TOR) it is quite effective.
Problem: The Law in every jurisdiction
Every Government on the planet reserves the right to legislate on people’s use of the Internet, and exercises it to varying degrees. The Government of the U.S.A., instrumental in the development of the Internet, reserves quite ridiculous authority to interfere, and uses and abuses this with aplomb.
Solution: Stay in the EU/become an EU citizen
Amazingly, the EU, the latest political hegemony in the most consistently abusive collective polity in human history, is now the bastion of Human Freedom. It is actually becoming quite effective in this role, and improving all the time.
Solution: Enforce Human Rights Law
‘Article 12.
No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks.’
Problem: Web Services and Social Media
The entire business model of providing web services (email in your browser, for example) and social media is to monetise the data you give up by using these services.
Solution: Don’t, just don’t (at least not yet)
There are a small number of privacy-respecting web-services/social media organisations that provide most, but not all, of what we expect from these systems. They are still young, suffer from technical and User Experience problems, and have yet to achieve critical mass. In a few years, perhaps sooner, the landscape will be very different. Instead, just give people a ring, or write them a postcard, or just make sure to look them up next time you are near. If everyone reaches out the world becomes small.
The Electronic Freedom Foundation provides the best overall guide to being safe online. Read more here.